Researchers from the University of Florida and North Carolina State University conducted an extensive analysis across seven LTE implementations, including Open5GS, Magma, and OpenAirInterface, and three 5G implementations.
The researchers uncovered 119 vulnerabilities in LTE & 5G Implemetations that let attackers remotely compromise and access the cellular core.
Every system tested was found to multiple critical flaws, some of which could enable attackers to disrupt entire metropolitan areas or gain unauthorized access to core cellular networks.
100+ Vulnerabilities in LTE & 5G Implementations
Each of the identified vulnerabilities has the potential to cause persistent denial of service (DoS) at a city-wide level.
By exploiting these flaws, attackers could crash critical components like the Mobility Management Entity (MME) in LTE or the Access and Mobility Management Function (AMF) in 5G networks.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup – Try for Free
Alarmingly, such attacks can be initiated by sending a single malicious data packet over the network—no SIM card or authentication is required.
This disruption could persist until network operators identify and patch the exploited vulnerability, leaving millions without access to phone calls, messaging, or data services.
The vulnerabilities are not limited to open-source platforms; proprietary systems deployed in commercial networks are equally affected. This highlights a systemic issue across both public and private cellular infrastructure.
Remote Access Risks: A Gateway for Espionage and Sabotage
Beyond service disruption, several vulnerabilities allow for buffer overflows and memory corruption, enabling attackers to infiltrate the cellular core network. Once inside, adversaries could:
– Monitor location and connection data for all subscribers within a city.– Conduct targeted attacks on specific individuals.– Compromise critical network components like the Home Subscriber Service (HSS) or Unified Data Management (UDM), potentially extending disruptions nationwide.
The researchers demonstrated this risk by developing a proof-of-concept remote code execution (RCE) exploit targeting one of the vulnerabilities in SD-Core.
Two Threat Models Identified
The study categorizes these vulnerabilities into two primary threat models:
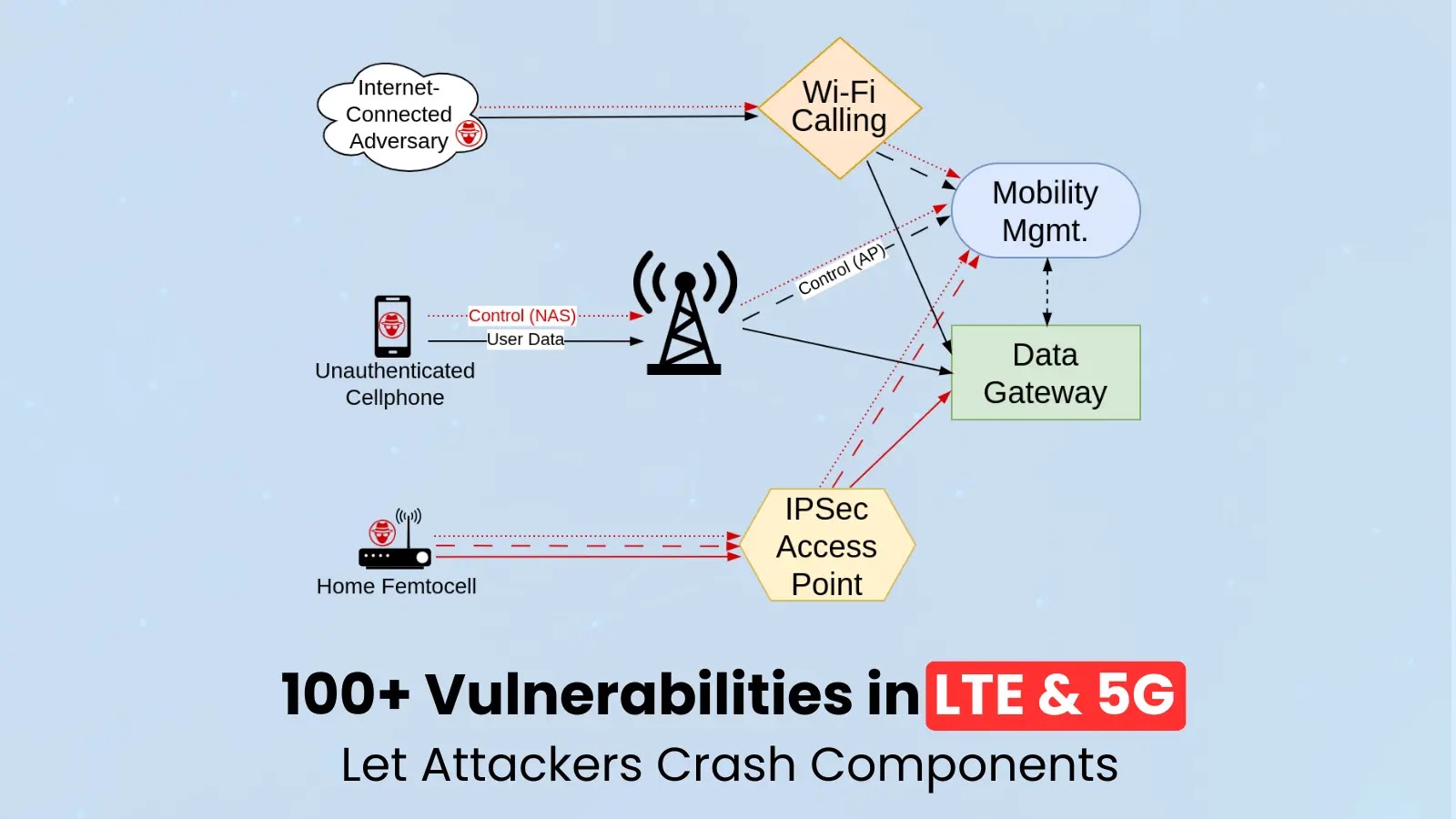
1. Unauthenticated Device Exploits: Attackers can exploit these vulnerabilities using any mobile device capable of sending malformed packets. With the rise of Wi-Fi Calling services, such attacks can now be launched remotely over the internet, bypassing traditional geographic limitations.
2. Base Station Exploits: Adversaries with access to compromised base stations or femtocells can exploit misconfigurations or leaked IPsec keys to infiltrate the cellular core. The proliferation of smaller 5G base stations in accessible locations further increases this risk.
The researchers adhered to responsible disclosure protocols, notifying affected vendors and allowing a 90-day window for patches before publicizing their findings.
In cases where vendors failed to respond—such as NextEPC and SD-Core—the team released patches directly through GitHub alongside their public disclosure.
Cellular networks are integral to modern life, supporting emergency services, businesses, and personal communication.
The ability to disrupt these networks at scale represents a significant threat to public safety and national security.
As 5G adoption accelerates, its integration with legacy LTE infrastructure exacerbates these vulnerabilities, making robust security measures imperative.
This research underscores the need for proactive security measures across the telecommunications industry.
Regular vulnerability assessments, adoption of zero-trust architectures, and stringent security protocols are essential to safeguarding critical infrastructure from increasingly sophisticated cyber threats.
Without immediate action, the promise of next-generation connectivity could be overshadowed by its vulnerabilities.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar