The Android boot chain initiates with the “Boot ROM,” which initializes the “bootloader.” The bootloader then loads the kernel, which is…
Category: Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting SolarWinds Web Help Desk…
GitHub has released security updates for Enterprise Server (GHES) to address multiple issues, including a critical bug that could allow…
Hackers exploit security vulnerabilities in the wild primarily to gain ‘unauthorized access to systems,’ ‘steal sensitive data,’ and ‘disrupt services.’…
A critical security vulnerability in Microsoft Dataverse has been discovered, allowing authorized attackers to elevate their privileges over a network.…
The maintainers of the Jetpack WordPress plugin have released a security update to remediate a critical vulnerability that could allow…
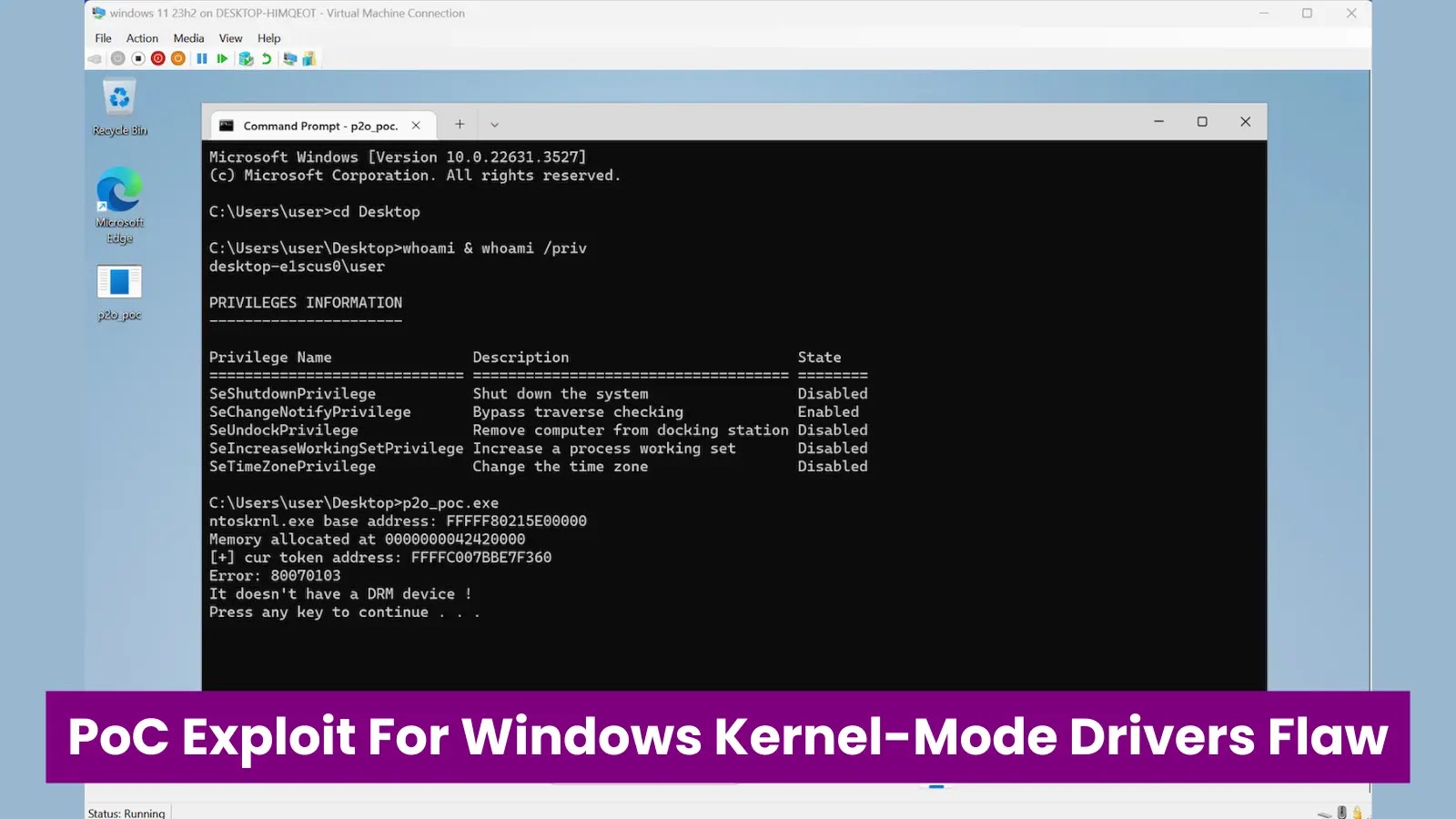
A critical vulnerability in Windows Kernel-Mode Drivers has been exposed with the release of a Proof-of-Concept (PoC) exploit, allowing attackers…
A sophisticated supply chain attack has been identified, leveraging entry points in popular open-source package repositories, including PyPI (Python), npm…
The link between detection and response (DR) practices and cloud security has historically been weak. As global organizations increasingly adopt…
A suspected nation-state adversary has been observed weaponizing three security flaws in Ivanti Cloud Service Appliance (CSA) a zero-day to…