We continue to expand the scope of our assurance programs at Amazon Web Services (AWS) and are pleased to announce…
Category: aws-news
aws-news
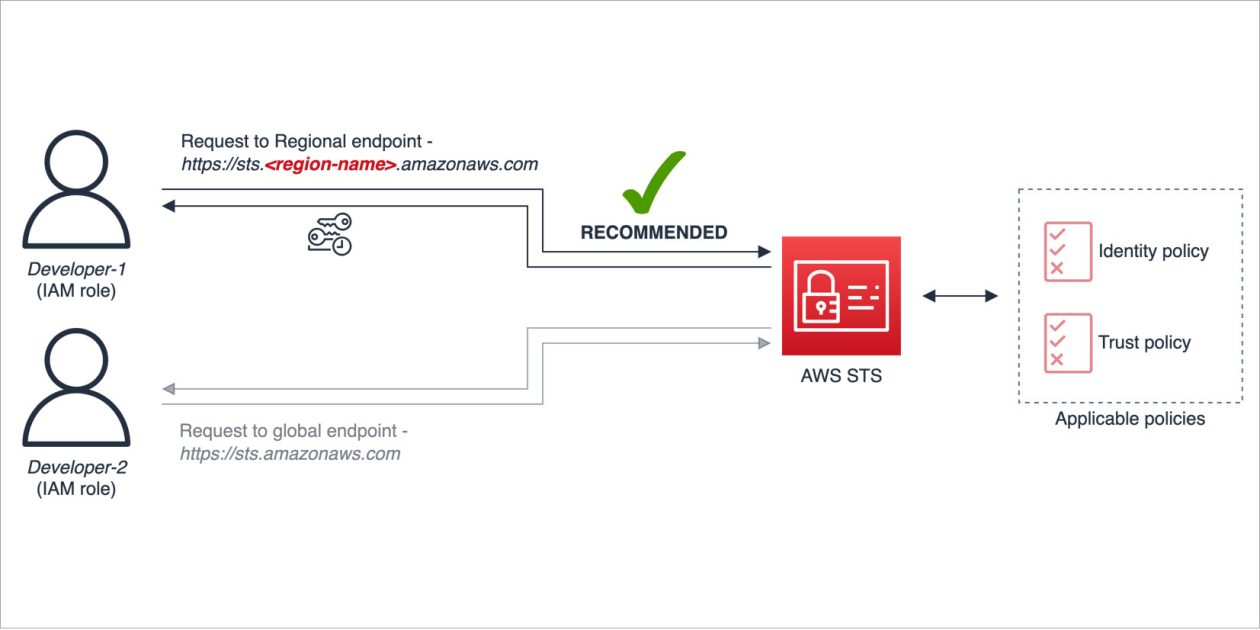
= “us-east-2” os.environ[“AWS_STS_REGIONAL_ENDPOINTS”] = “regional” You can use the metadata attribute sts_client.meta.endpoint_url to inspect and validate how an STS client…
When building API-based web applications in the cloud, there are two main types of communication flow in which identity is…
Introducing AWS Customer Compliance Guides: Simplifying Compliance Mapping for AWS Services
The AWS Global Security & Compliance Acceleration (GSCA) Program has released AWS Customer Compliance Guides (CCGs) on the AWS Compliance Resources…
Introducing AWS HITRUST SRM Version 1.4.2: Enhanced Support for CSF v11.2 Assessments and Control Inheritance
The latest version of the AWS HITRUST Shared Responsibility Matrix (SRM)—SRM version 1.4.2—is now available. To request a copy, choose…
Stripe API Keys Exposed in Amazon S3 Bucket: Security Breach Mitigated
Several customers who use Amazon Web Services (AWS) are utilizing Stripe global payment services to accelerate product development and increase…
Automating Network Firewall Rule Management in AWS Centralized Deployment Solution
AWS Network Firewall is a stateful managed network firewall and intrusion detection and prevention service designed for the Amazon Virtual…
How Amazon Verified Permissions Enables Access Control in SaaS Applications
Access control is a crucial aspect of multi-tenant software as a service (SaaS) applications. Developers of SaaS applications must be…
Uncovering Nested Java Dependencies: How Amazon Inspector Enhances Visibility and Mitigation
Amazon Inspector is an automated vulnerability management service that scans Amazon Web Services (AWS) workloads for software vulnerabilities and unintended…
Maximizing Security and Efficiency: The Power of IAM Role Paths
AWS promotes the use of IAM roles over IAM users for better security practices, as IAM roles are designed to…