Google has rolled out a critical security update for its Chrome browser, addressing a severe flaw that could lead to…
Author: sysops
A recent discovery has unveiled vulnerabilities in multiple hosted, outbound SMTP servers, allowing authenticated users and certain trusted networks to…
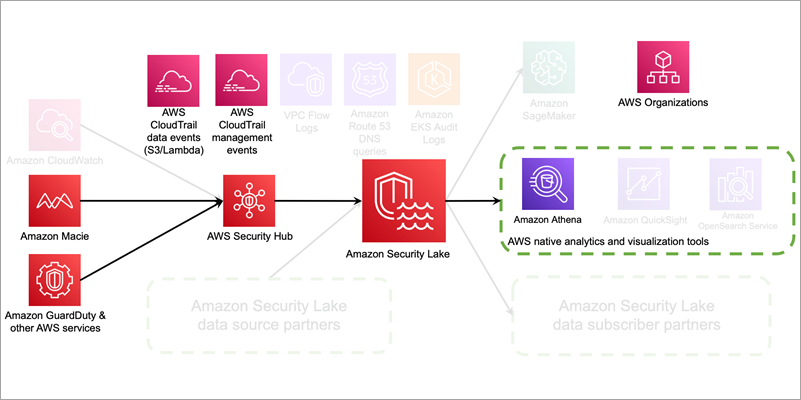
Many customers use Amazon Security Lake to automatically centralize security data from Amazon Web Services (AWS) environments, software as a…
Progress Software has disclosed a new high-severity vulnerability in its MOVEit Transfer file transfer solution that could allow attackers to…
Amazon Web Services (AWS) is pleased to announce that we have revalidated our AAA rating for the Pinakes qualification system.…
Microsoft researchers have found a critical vulnerability in VMware’s ESXi hypervisors. Ransomware operators are using this problem to attack systems.…
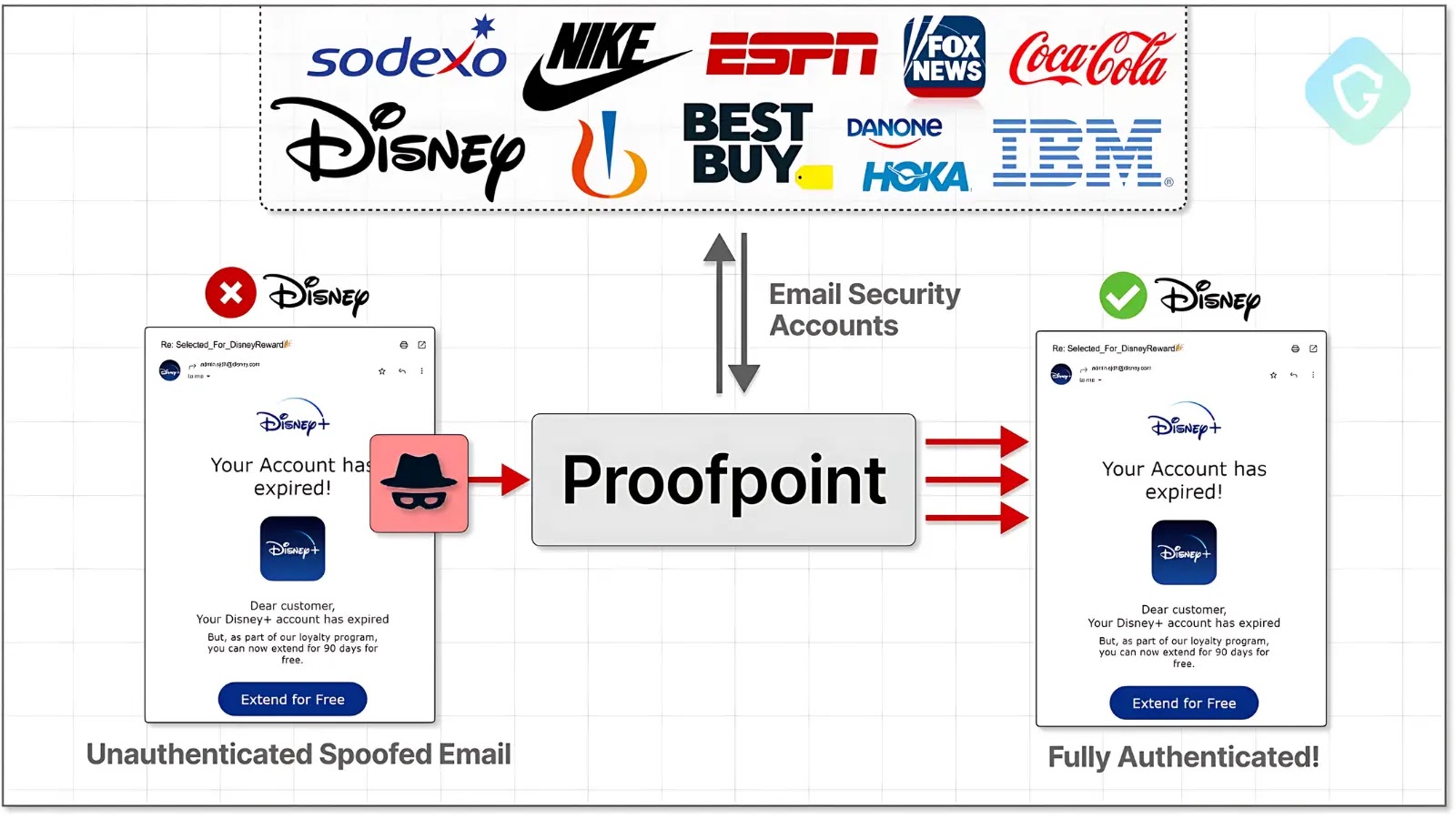
A massive phishing campaign dubbed “EchoSpoofing” has exploited a critical vulnerability in Proofpoint’s email protection service, allowing cybercriminals to send…
This blog post is the second of a two-part series where we show you how to respond to a specific…
By exploiting OS command injection vulnerabilities, threat actors can run arbitrary commands on a host operating system to obtain unauthorized…
Cloud security giant Wiz has detailed a campaign in which threat actors have targeted exposed Selenium Grid instances for cryptocurrency…