Throughout software development, robust security and compliance measures are required, especially in industries like financial services where data integrity and…
Author: sysops
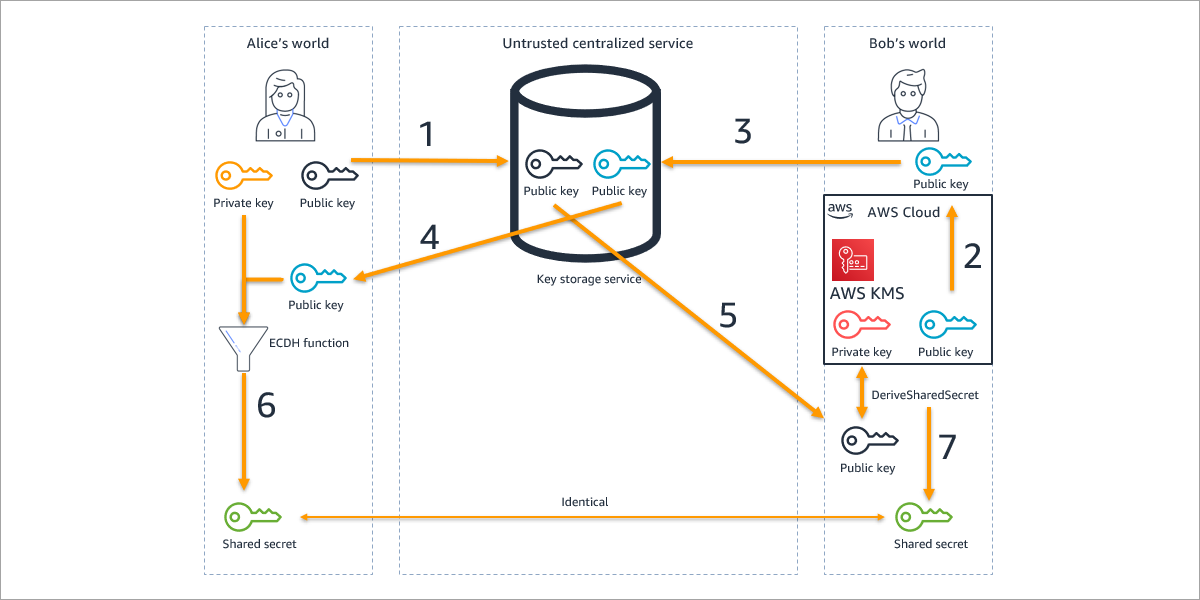
When using cryptography to protect data, protocol designers often prefer symmetric keys and algorithms for their speed and efficiency. However,…
Amazon Web Services (AWS) customers operating in a regulated industry, such as the financial services industry (FSI) or healthcare, are…
Cisco Talos has identified eight security vulnerabilities in Microsoft applications running on the macOS operating system, raising concerns about potential…
A recent analysis of a security vulnerability in Microsoft’s Secure Channel revealed a critical flaw that could be exploited for…
, “detail-type”: [“GuardDuty Malware Protection Object Scan Result”], “detail”: { “scanStatus”: [“COMPLETED”], “resourceType”: [“S3_OBJECT”], “s3ObjectDetails”: { “bucketName”: [“”] }, “scanResultDetails”:…
Security researchers at Palo Alto Networks have spotted a threat actor extorting organizations after compromising their cloud environments using inadvertently…
Researchers at Tenable have identified vulnerabilities in Microsoft’s Azure Health Bot Service that threat actors could have been able to…
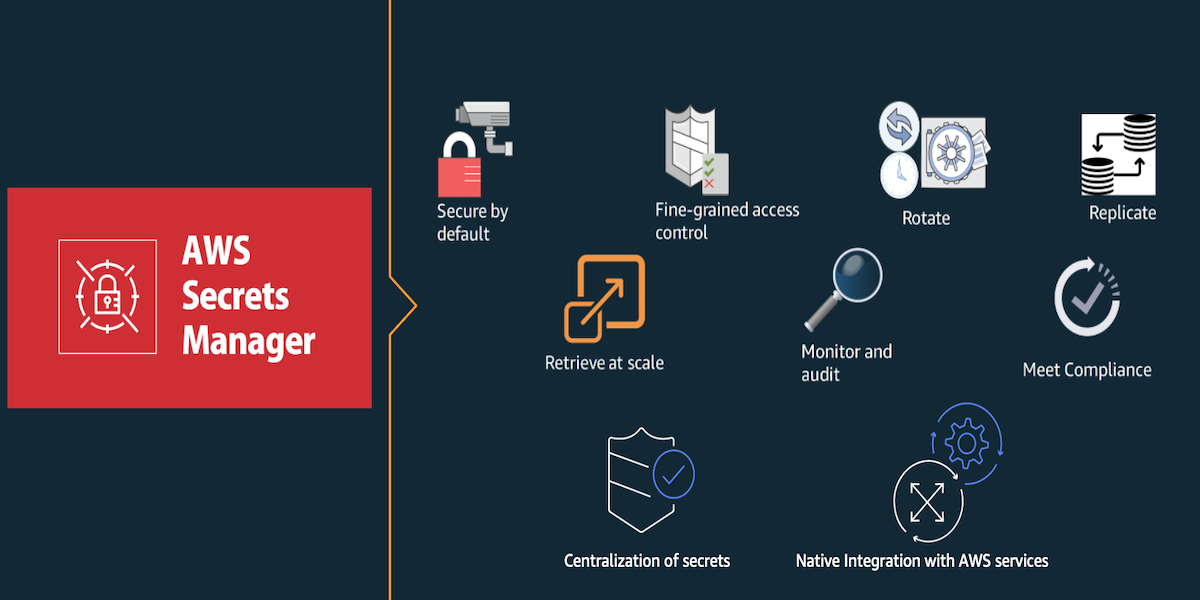
In today’s digital landscape, managing secrets, such as passwords, API keys, tokens, and other credentials, has become a critical task…
Customers use Amazon Web Services (AWS) to securely build, deploy, and scale their applications. As your organization grows, you want…