For businesses that handle sensitive customer information, achieving SOC 2 (System and Organization Controls 2) compliance is not just a…
Author: sysops
A new ransomware threat dubbed “Helldown” has emerged, actively exploiting vulnerabilities in Zyxel firewall devices to breach corporate networks. Cybersecurity…
The Open Security Controls Assessment Language (OSCAL) is a project led by the National Institute of Standards and Technology (NIST)…
Developers play a critical role in ensuring banks remain competitive and compliant. One framework gaining significant attention is DORA. If…
DevSecOps streamlines software development by allowing teams to ship features quickly and providing short feedback cycles for customers. These short…
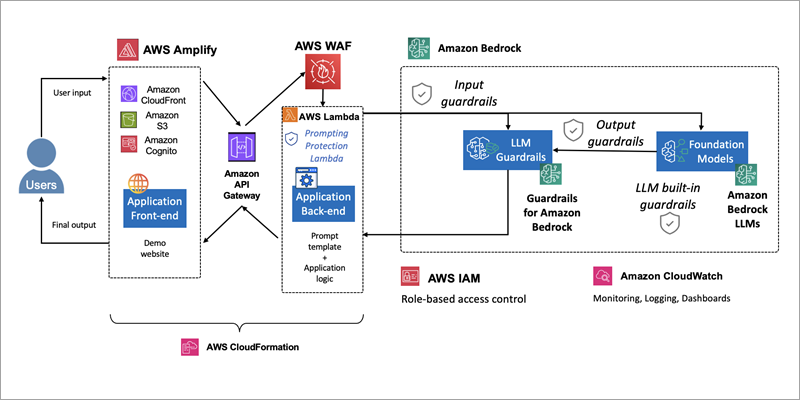
Generative AI applications have become powerful tools for creating human-like content, but they also introduce new security challenges, including prompt…
A critical vulnerability has been identified in Apache CXF, a widely used open-source framework for web services. This flaw, tracked…
A recently identified vulnerability in the Brave browser has raised significant security concerns for its users. The issue, tracked as…
Cybersecurity researchers have identified significant vulnerabilities within the Mercedes-Benz User Experience (MBUX) infotainment system, leading to unauthorized remote access capabilities. …
A critical vulnerability (CVE-2024-13454) has been identified in Easy-RSA versions 3.0.5 through 3.1.7 when used with OpenSSL 3. This flaw…