Artificial intelligence (AI) is quickly becoming the backbone of modern software development, fueling developer efficiency and accelerating innovation. With the…
Author: sysops
This blog post is the second post in a series about GitLab Universal Automated Response and Detection (GUARD). Writing and…
A significant cybersecurity threat has emerged as hackers on a prominent Russian dark web forum claim to be selling an…
Researchers have uncovered two critical vulnerabilities in Apple’s custom silicon chips, dubbed SLAP (Speculative Load Address Prediction) and FLOP (False…
A proof-of-concept (PoC) exploit for the actively exploited Windows Common Log File System (CLFS) vulnerability, tracked as CVE-2024-49138 has been…
WhatsApp’s “View Once” option is one of the privacy features in the instant messaging space that is intended to provide…
A Cross-Site Scripting (XSS) vulnerability has been identified in the TP-Link Archer A20 v3 router, specifically in firmware version 1.0.6…
A significant zero-day vulnerability in Zyxel CPE series devices, identified as CVE-2024-40891, is being actively exploited by attackers. This vulnerability…
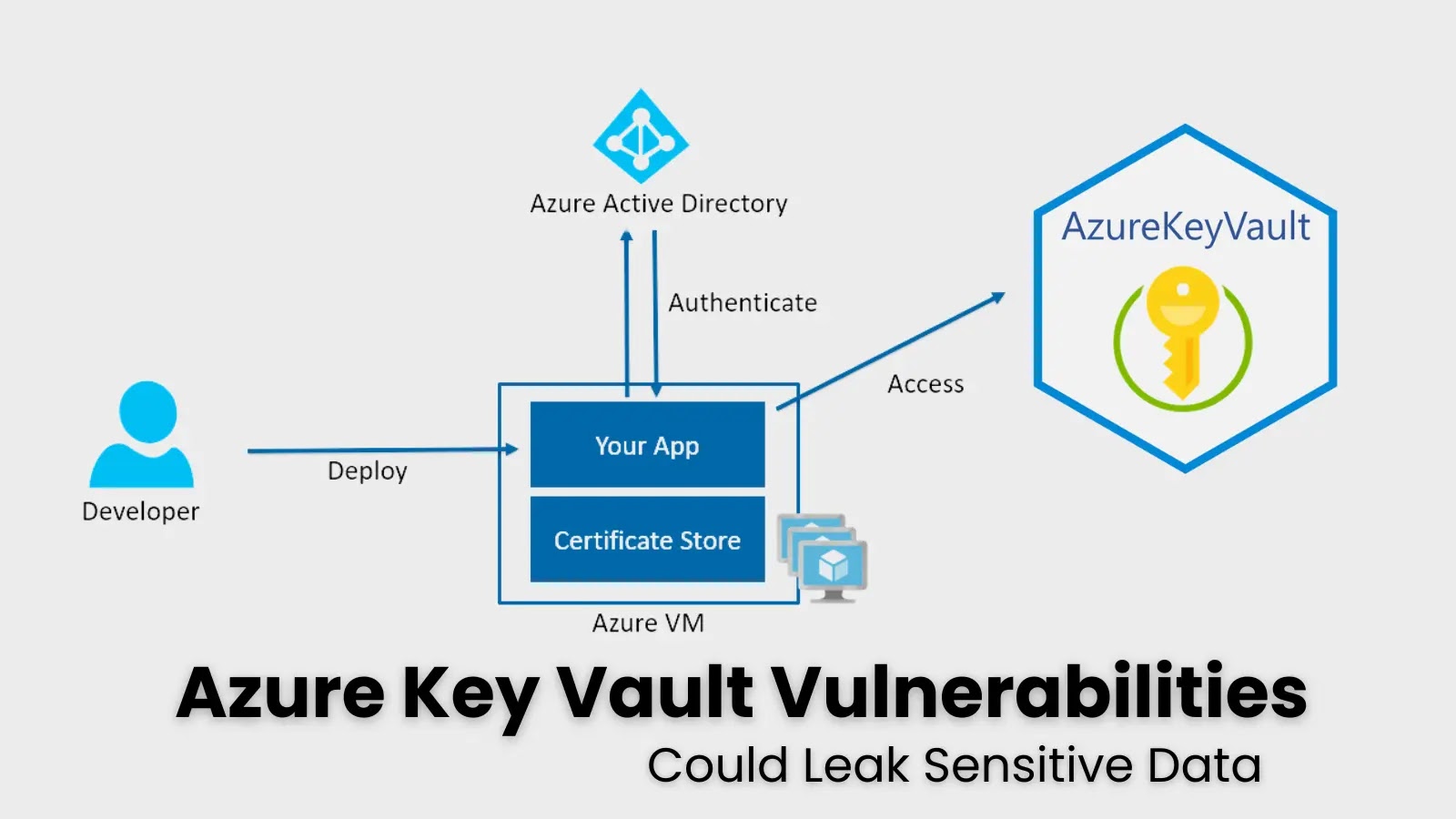
A detailed walkthrough demonstrates how attackers can manipulate Azure Key Vault’s access policies after compromising Entra ID (formerly Azure AD)…
Amazon GuardDuty is a threat detection service that continuously monitors, analyzes, and processes Amazon Web Services (AWS) data sources and…